 A Hitch-Hacker’s Guide to the Galaxy – Developing a Cyber Security Roadmap for Executive Leaders
A Hitch-Hacker’s Guide to the Galaxy – Developing a Cyber Security Roadmap for Executive Leaders
In this blog series, I am looking at steps that your organisation can take to build a roadmap for navigating the complex world of cyber security and improving your cyber security posture.
There’s plenty of technical advice out there for helping security and IT teams who are responsible for delivering this for their organisations. Where this advice is lacking is for executive leaders who may or may not have technical backgrounds but are responsible for managing the risk to their organisations and have to make key decisions to ensure they are protected.
This blog series aims to meet that need, and provide you with some tools to create a roadmap for your organisation to follow to deliver cyber security assurance.
Each post focuses on one aspect to consider in your planning, and each forms a part of the Cyber Security Assessment service which we offer to our member organisations in the UK Higher and Further Education sector, as well as customers within Local Government, Multi-Academy Trusts, Independent Schools and public and private Research and Innovation. To find out more about this service, please contact your Relationship Manager, or contact us directly using the link above.
View all episodes.
Episode 13: Action stations!
“Don’t Panic. It’s the first helpful or intelligible thing anybody’s said to me all day.”
Douglas Adams, A Hitchhiker’s Guide to the Galaxy
[ Reading time: 11 minutes ]
At the start of this series, I mentioned that you should consider the likelihood of some sort of cyber related incident happening to your organisation to be 100% (it’s “when” not “if”). When that inevitable incident happens, it’s your Incident Response (IR) plan which will help get you through and return to business as usual.
The IR plan is one of three closely related plans; the others are Disaster Recovery (which I covered in episodes 11 and 12—“Be the Master of Disaster”) and Business Continuity (which I’ll discuss in the next episode—“Keeping the Lights On”).
Incident response is about more than just cyber security, though. It applies to any major incident which poses a significant risk to life, property, or business operations and which requires a special response.
So in your IR planning, you should be considering fire, flood, other natural disaster, illness outbreak and terrorist threat, alongside cyber incidents.
Thankfully, we can lean on well-developed incident response procedures from the emergency services to help guide best practices.
1. If you fail to plan…
The first, and perhaps very obvious, step is to have a plan. A well structured, well thought through plan makes handling a major incident much more manageable, especially with the pressure and stress that comes with it. The plan needs to be up-to-date (you should be reviewing it annually at a minimum) and accessible, both online and offline.
Remember that in the event of a cyber incident, you may not be able to log in to systems, so you need to ensure your IR plan is available by other means. Paper is a great backup technology for this.
2. Trigger happy
Your plan should have some basic elements which are applicable to all major incidents.
You need to define what you mean by an “incident” and how the IR process is activated. When and how does an adverse “event” escalate to being an incident that triggers the plan? Your plan should define the terms, with examples, and have a clear flowchart which indicates how and who activates the plan.
3. Who’s on first base?
Your plan should clearly define roles and responsibilities. It’s helpful to define 3 levels of response to handle different aspects of the incident. These are often called Gold, Silver and Bronze teams (terms used by the emergency services). The Gold team comprises senior leaders who will make the key high-level response decisions and manage communications to stakeholders. The Silver team will be business function managers who will ensure that the various aspects of the business respond appropriately. The Bronze team provide the “boots on the ground” operational response—in a cyber incident, that’s going to be your IT and cybersecurity team.
There should be a named individual on the Gold team in overall charge of the incident. And make sure that the plan assigns people to deputise in the event that key leaders are unavailable.
If it’s practical, it’s a good idea to have one or more locations designated as “war rooms” where response teams can be based. This ensures that teams are fully focussed on the response and helps with keeping everyone fully briefed and up-to-date.
4. Communication is key
Good communication is absolutely critical to effective incident response. Everyone in the organisation needs to understand what is going on and what they need to do. There need to be clearly defined channels of communication between Gold, Silver and Bronze response teams. You must have contact information for all your key internal and external contacts included in the plan, and these need to be checked and updated regularly.
Remember that an incident may knock out some of your normal channels of communication. Think about how you will communicate if you have no email, no Teams, no internet access, or no mobile phone signal.
Only authorised people should be communicating to the media, which should be handled by the Gold team alongside the Communications team. But remember, it’s next to impossible to prevent information getting out on social media, especially from the student body, so you want to be ahead of the game and control the messaging.
5. Build your playbooks
Although all major incidents have common response features, there are particular characteristics which are unique to each type. For a terrorist threat you may have lock-down procedures you need to invoke, whereas for a cyber incident you may have a ransom demand to consider.
It is helpful to record the particular response considerations for each of these in a separate playbook for each, which is normally an appendix to the main IR plan. Having these available means you ensure that no issues are overlooked, and provide a template for decision-making processes.
6. Exercise regularly
No plan survives contact with the enemy. That’s the long-established military slogan and for a reason. However well though-out your plan, you’ll only discover its flaws when you put it into practice. And far better to discover these in “peace time” than in the heat of a real incident. Table-top exercises are excellent for this, if well-structured. We recommend doing these annually, for one of the playbook scenarios in the IR plan. While you can run these exercises yourself, it’s often valuable to bring in a third-party facilitator who can ask awkward questions and expose the blind spots in your planning.
For cyber incident response exercises, NCSC have the Exercise in a Box toolkit, and at Jisc we offer a Ransomware Incident Response Workshop where we act as facilitators.
7. Lessons learned
The NCSC has published some excellent advice on incident response planning which is summarised by this very nice infographic.
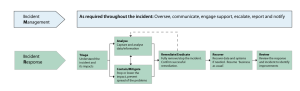
While the incident response cycle is generally well understood, the final review (or “lessons learned”) stage is often overlooked. Whether you are running an incident response testing exercise or doing it for real, there will be things that went well, and things that didn’t. Take time to review this with all relevant stakeholders, and update your plan or playbook accordingly.
A Final [Deep] Thought
In the next episode of A Hitch-Hacker’s Guide to the Galaxy, we’ll be looking at business continuity and resilience. Keeping the lights on.
For now, you can take useful steps forward by checking out your organisation’s incident response planning. Do you have an IR plan? When was it last updated? Does it contain all the elements required? Do you have playbooks for each scenario type? When was it last tested?
